Don’t want Windows 10 forced upon you?

Well in my opinion, the word “forced” isn’t quite accurate.
Somewhere along the line, the End User has “Reserved” their copy of the free Windows 10 upgrade, which has subsequently set them on a path that, along with ongoing Windows updates, lead to an apparently automated upgrade to Windows 10.
Now whilst it is true that you can “Roll Back” Windows 10, there may be some consequences. The first of which is the time taken whilst the upgrade takes place, and the second is the time taken to roll it back.
The other consequence is the possible loss of data.
I had one customer who claimed to have lost all his Favorites.
So what to do if you want to stop those Windows 10 upgrade notifications?
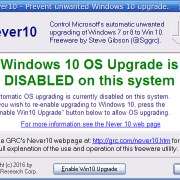
Well I have come across a free little utility called Never10.
When run, it will disable the Windows 10 upgrade notifications.
So if you have had enough of the persistent Windows 10 upgrade notifications, give it a try.
You can download it from https://www.grc.com/never10.htm


 This will not please a lot of my customers, but it had to happen sooner or later.
This will not please a lot of my customers, but it had to happen sooner or later.
 I am constantly telling people and Business Owners of the importance of having a sound Backup Strategy. I cannot stress enough that if you have important data on your Computer, and if you or your Business lives or dies by that data, you need to have an effective backup strategy in place.
I am constantly telling people and Business Owners of the importance of having a sound Backup Strategy. I cannot stress enough that if you have important data on your Computer, and if you or your Business lives or dies by that data, you need to have an effective backup strategy in place.
 OK, so similar to
OK, so similar to 
 Well here is a handy website to know about.
Well here is a handy website to know about.


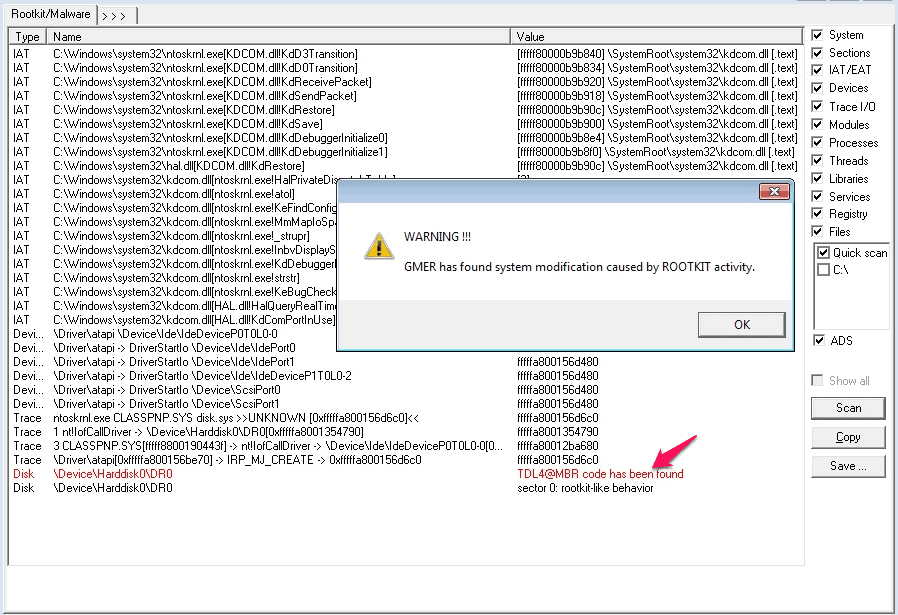
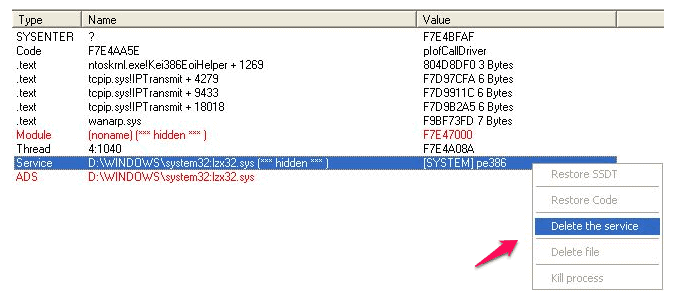
 I recently had a Laptop in the workshop that had a particularly difficult to remove Rootkit Virus installed on it.
I recently had a Laptop in the workshop that had a particularly difficult to remove Rootkit Virus installed on it.